 Cybersecurity researchers have developed what’s the first fully undetectable cloud-based cryptocurrency miner leveraging the Microsoft [Azure Automation](https://learn.microsoft.com/en-us/azure/automation/overview) service without racking up any charges.Cybersecurity company SafeBreach said it discovered three different methods to run the miner, including one that can be executed on a victim’s environment without attracting any attention.“While this research is significant because of its potential impact on cryptocurrency mining, we also believe it has serious implications for other areas, as the techniques could be used to achieve any task that requires code execution on Azure,” security researcher Ariel Gamrian [said](https://www.safebreach.com/blog/cryptocurrency-miner-microsoft-azure) in a report shared with The Hacker News.The study mainly set out to identify an “ultimate crypto miner” that offers unlimited access to computational resources, while simultaneously requiring little-to-no maintenance, is cost-free, and undetectable.That’s where Azure Automation comes in.
Cybersecurity researchers have developed what’s the first fully undetectable cloud-based cryptocurrency miner leveraging the Microsoft [Azure Automation](https://learn.microsoft.com/en-us/azure/automation/overview) service without racking up any charges.Cybersecurity company SafeBreach said it discovered three different methods to run the miner, including one that can be executed on a victim’s environment without attracting any attention.“While this research is significant because of its potential impact on cryptocurrency mining, we also believe it has serious implications for other areas, as the techniques could be used to achieve any task that requires code execution on Azure,” security researcher Ariel Gamrian [said](https://www.safebreach.com/blog/cryptocurrency-miner-microsoft-azure) in a report shared with The Hacker News.The study mainly set out to identify an “ultimate crypto miner” that offers unlimited access to computational resources, while simultaneously requiring little-to-no maintenance, is cost-free, and undetectable.That’s where Azure Automation comes in.
Developed by Microsoft, it’s a cloud-based automation service that allows users to automate the creation, deployment, monitoring, and maintenance of resources in Azure.SafeBreach said it found a bug in the [Azure pricing calculator](https://azure.microsoft.com/en-us/pricing/calculator/) that made it possible to execute an infinite number of jobs totally free of charge, although it relates to the attacker’s environment itself.Microsoft has since issued a fix for the problem.
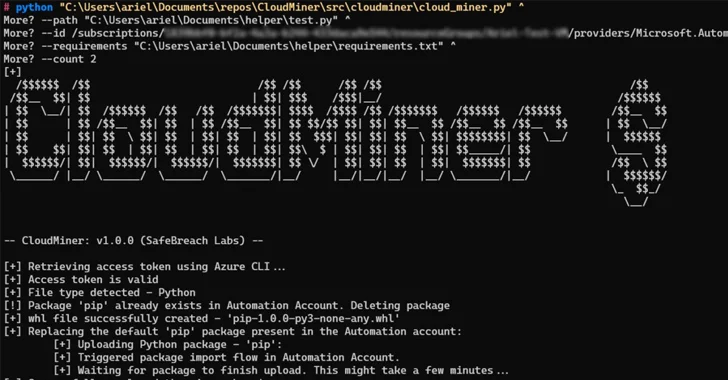
An alternative method entails creating a test-job for mining, followed by setting its status as “Failed,” and then creating another dummy test-job by taking advantage of the fact that only one test can run at the same time.The end result of this flow is that it completely hides code execution within the Azure environment.A threat actor could leverage these methods by establishing a reverse shell towards an external server and authenticating to the Automation endpoint to achieve their goals.Furthermore, it was found that code execution could be achieved by leveraging Azure Automation’s feature that allows users to upload custom Python packages.“We could create a malicious package named ‘pip’ and upload it to the Automation Account,” Gamrian explained.“The upload flow would replace the current pip in the Automation account.
After our custom pip was saved in the Automation account, the service used it every time a package was uploaded.” SafeBreach has also made available a proof-of-concept dubbed [CoinMiner](https://github.com/safebreach-labs/cloudminer) that’s designed to get free computing power within Azure Automation service by using the Python package upload mechanism.Microsoft, in response to the disclosures, has characterized the behavior as “by design,” meaning the method can still be exploited without getting charged.
While the scope of the research is limited to the abuse of Azure Automation for cryptocurrency mining, the cybersecurity firm warned that the same techniques could be repurposed by threat actors to achieve any task that requires code execution on Azure.“As cloud provider customers, individual organizations must proactively monitor every single resource and every action being performed within their environment,” Gamrian said.“We highly recommend that organizations educate themselves about the methods and flows malicious actors may use to create undetectable resources and proactively monitor for code execution indicative of such behavior.” Nov 08, 2023NewsroomPrivacy / Data Security Meta-owned WhatsApp is officially rolling out a new privacy feature in its messaging service called “Protect IP Address in Calls” that masks users’ IP addresses to other parties by relaying the calls through its servers.“Calls are end-to-end encrypted, so even if a call… (CLICK READ MORE) [Read more](https://beker.uk/2023/11/08/whatsapp-introduces-new-privacy-feature-to-protect-ip-address-in-calls/) Nov 08, 2023NewsroomSupply Chain / Software Security A new set of malicious Python packages has slithered their way to the Python Package Index (PyPI) repository with the ultimate aim of stealing sensitive information from compromised developer systems.
The packages masquerade as seemingly innocuous obfuscation tools, but harbor a piece of… (CLICK READ MORE) [Read more](https://beker.uk/2023/11/08/beware-developers-blazestealer-malware-discovered-in-python-packages-on-pypi/).
